CYBERWARS's Pearl Harbour
"Server not found"
or
"Connection timed out"
For Weeks:

Map By major ISP's.
no bombs, rootkits, explosions, hacking or announcement of war.
The Internet is designed to survive a nuclear attack to a few countries.
If a Continent or two are taken out by nuclear attacks the Internet will automatically rout around the missing pieces.
A DOS attack , as we know it now, targets a single URL, floods it with traffic
so visitors cannot get in.
A bot attack form a botnet, thousands of zombie computers attacking the one URL.
But suppose a Government with millions of zombie computers flooded a high volume Internet hub, and the hub above it and below it.
Ok now pick out a thousand of the key hubs to flood, with millions of botnets.
Now the traffic will try and work its way around the blockage and over welm some of the Internet shortcuts.
The effect would be some of the hubs would go down, and some would turn high speed T1 lines into dialup speeds.
The cascading effects could take out land line phones, cable TV, automated radio stations, back up banking transactions, close down shopping carts...
The traffic on the outer rings, and short cuts between hubs would also be flooded by the traffic routing around the blockages.
Are there a Million botnets out there?
WE DON'T KNOW, WE ONLY COUNT THE ACTIVE BOTNETS.
As a nation state someone could create 100,000 bots a day test 1,000 of them and let the rest sleep. No one would ever know about the sleeping botnets till they came on line.
Wait for the traffic to route around the blockages then take out another 1000 hubs, based on traffic patterns, for maximum effect.
The Internet could not be shut down, but the traffic making its way through the internet could be cut down this way by many many factors.
 Black nodes are "MIL" 1998
Black nodes are "MIL" 1998
Our current measurement system does not account for "sleeper bots", only active bots.

 Close up, your PC would be at the end of one of those white lines.
Close up, your PC would be at the end of one of those white lines.
Think your PC is slow now??
USA is not ready for this, nor does USA have this offensive capability.
Lots of work to do.
Gerald
UPDATE:
The most significant attack in recent years came on Feb. 6, when six of 13 root-zone servers were slammed by an army of “zombie computers,” which were compromised by hackers, the Cardozo Law School professor said at the think tank event.
October 22 2002 Nine of the internet's 13 "root DNS" servers are disabled in a massive attack by a bot herder advertising his services.
2006 Peer-to-peer communication protocols pass command of the botnet between compromised PCs to evade bot hunters. Automated retaliatory attacks start on anything trying to find or interfere with a botnet.
SOURCE:
xxxxxxxxxxxxxxxxxxxxx
China ‘has .75M zombie computers’ in US19 Sep 2007 by google soft
China ‘has .75M zombie computers’ in US. A former senior US information security official says there are nearly three-quarter million personal computers in the United States taken over by Chinese hackers. ...
xxxxxxxxxxxxxxxxxxxxxx
CHINESE HACKER:
Tan Dailin lets out an audible gasp when he is told that he was identified in the U.S. as someone who may have been responsible for recent security breaches at the Pentagon. "Will the FBI send special agents out to arrest me?" he asks. Much as they might want to talk with him, though, FBI agents don't have jurisdiction in Chengdu, the capital of China's Sichuan province, where Tan lives.
SOURCE: time inc
Gerald
Anthropologist
Hackers we have taken out: Here
The useful future of Cyber warfare.
WWW Terrain Map
Worst CASE:
Internet status check
RED ALERT new WWW attack paradigm
Internet Anthropologist available for Blog interview, Phone consult: or lecture.
UPDATE: 12.17.07
The suspicion remains that botnet time was rented to attack Estonia from Russian trans-national criminal syndicates and when this time ran-out the attacks fell-off. Since January 2007 numerous computers have been infected by a virus known as, Storm Worm, giving the criminal syndicates controlling the virus and hence the computers, processing power estimated beyond the power of the worlds top ten supercomputers. There is clearly an argument for using these botnet systems for more than just spam. It is not yet true to say that the next conflict will be fought virtually on computers alone but it may be rehearsed there.
SOURCE:
xxxxxxxxxxxxxx
UPDATE: 12.18.07
A senior Estonian official recently said for the first time that the cyberattacks earlier this year against his country's government and commercial Internet infrastructure were carried out using a network of computers infected with special hacker software that had been rented from a criminal syndicate.
Jaak Aaviksoo, the Estonian minister of defense, told a Washington audience last month that the botnet that attacked Estonia was "rented for that purpose and rented (from) clearly illegal groups that have hijacked a number of computers worldwide."
SOURCE:
UPDATE: 12.18.07
....
Ridentem dicere verum quid vetat....
FSB ( Russia ), HOW LONG BEFORE THE TALKING BOTS MIGRATE TO THE CELL PHONES? Phone service DDOS?
g
New threat matrix.
Update:01.08.07
The Strategy Page describes how China assembled a force few have heard about. In idyllic 1990s, the Chinese Defense Ministry established a research organization called the "NET Force" geared towards conducting information warfare. NET Force was soon joined by an irregular civilian militia; the "Red Hackers Union" (RHU). "Starting in the late 1990s, China assembled what has now become 30,000 Ministry of Public Security employees manning the Golden Shield Project (also known as The Great Firewall of China), and monitor Internet use throughout the country."
Future:
Infection and Survival
The initial infection of botnet client machines was done via worms, but soon the botnets began replicating themselves. Most botnets have the ability to self-update. The bot herder will issue an update command, and all his little troops will download and run new versions of themselves. This update mechanism is even more efficient than Windows update, and it's certainly frightening. Some viruses have also been known to disable antivirus software, and most users would never even notice. If a virus can successfully disable all defense mechanisms and then install undetectable bot client software, it's sure to survive.
The botnet itself is also a worm, because many bots have the ability to spread. They will try a fairly large arsenal of exploits against computers on the same network, or possibly even across the Internet. Bot clients updating themselves were primarily used as a mechanism to distribute new exploit code at first, but then something marvelous happened, and the first self-preservation behavior documented occurred recently: bot clients began DDoS'ing any computer that attempted to detect them by scanning. ( This cause the first massive attack against the NODES. It was an accident G)
Botnets have been dubbed "IRC Botnets" in the past, but this isn't completely accurate any longer. Some newfangled botnets still use IRC to communicate, but they do it over SSL. This essentially means that you cannot detect their presence. Furthermore, the old IRC model of "connect to a server" just isn't feasible. A distributed system that's dependent on a single server is useless, especially when that single server is a huge takedown target. Many a botnets were abandoned in the infancy stage of botnet evolution. We could see this with network anomaly detection tools quite easily: clients would appear as a TCP scanner when they unsuccessfully tried connecting to home-base over and over again.
At this point only one thing comes to mind: peer-to-peer applications. P2P networks have successfully thwarted the MPAA/RIAA, so it should work for botnets as well. Especially with their ability to replicate and attack back, they should be unstoppable. Indeed, there have been many reports of p2p botnet activity. Throw SSL in the mix, and they certainly are undetectable and unstoppable.
Let's think about this for a moment. If bots have the ability to self-update, self-preserve, and massively execute large parallel jobs at the command of a single person, what do we really have here? This is not just a tool for spamming and other ills; this is a living, breathing ecosystem.
SOURCE:
xxxxxxxxxxxxxxxxxxxxx
The result is that millions of business and home computers – some estimates put the figure as high as 300 million – have been taken over by global gangs of cyber criminals. They're being used every moment of the day for extortion, to spread child pornography and, most commonly, to spew out billions of unsolicited e-mails. It can – and has – brought down the internet for an entire country.
The problem is getting so bad, and accelerating so rapidly, some experts believe 2008 could even be the year the internet meets its Armageddon. On Christmas Eve and Hogmanay, unusually heavy botnet activity was reported, leading to speculation that a major attack was brewing.
SOURCE:
XXXXXXXXXXXXXXXX
Updated: 01.25.08
Malware Increased by 6 Orders of Magnitude from 2006 to 2007
xxxxxxxxxxxxxxx
YOU CAN SAVE THE INTERNET !
Another free security utility: Trend Micro’s RUBotted
ZDNet Blogs -Jan 11, 2008
RUBotted monitors for remote command and control (C&C) commands sent from a bot-herder to control your computer.
xxxxxxxxxxxxxxxx
PandaLabs: Half a Million Computers Infected with Bots Everyday
IT News Online Staff
2008-01-19
According to data compiled by PandaLabs in its annual report on malware activity in 2007, around half a million computers are infected by bots everyday.
Bots are programs that go resident on a computer awaiting commands from their creators, who can take complete control of the infected system. Once they have control over several hundred computers, cyber-crooks can hook them all up to create botnets.
The report said that approximately 11% of computers around the world are part of these botnets, and they are responsible for 85% of all spam sent.
SOURCE:
xxxxxxxxxxxxxxxxx
Couple a huge bot net attack with a physical cable attack:
( Internet failure hits two continents: Story Highlights: Extensive Internet failure has affected much of Asia, the Middle East, north Africa )
DUBAI, United Arab Emirates: 1.08 (CNN) -- Large swathes of Asia, the
>> Middle East and north Africa had their high-technology services
>> crippled Thursday following a widespread Internet failure which
>> brought many businesses to a standstill and left others struggling to cope.
Update: 3 cables cut in two days.
xxxxxxxxxxxxxxxxxx
DHS cyber storm test misses key TESTS. instant issues not pertinent.??
xxxxxxxxxxxxxxxxxxxxx
Is the Russian Business Network protected by the Federal'naya Sluzhba Bezopasnosti (FSB)? ( Internet Anthropologist hypothesised about this months ago.)
xxxxxxxxxxxxxxxx
American Teen with 400,000 bots.
xxxxxxxxxxxxxxxxxx
New class of WMD bots
xxxxxxxxxxxxxxxxxxx
There are defensive options, and offensive options, we have NOT discussed here.
Out of the Box solutions. Email me for details.
barb.andrews at gmail.com
UPDATE:12.28.2015
ISIS tried this through a Islamic News APP
NODES READY:NO PROBLEM
Gerald
Anthropologist
Tactical Internet Sys analyst.
AD MAGNUM
.
Botmaster owns up to 250,000 zombie PCs (9 November 2007)
Alleged CastleCops DDoS botmaster busted (3 October 2007)
FBI logs its millionth zombie address (13 June 2007)
Florida 'botmaster' charged with Akamai DDOS attack (24 October 2006)
Botnet master jailed for five years (9 May 2006)
Bot herder pleads guilty to 'zombie' sales (24 January 2006)
Suspected bot master busted (4 November 2005)
35 million bots and counting, 03,07.09
.
18-year-old alleged botnet king appears in New Zealand court
DHS gives itself a 'C' for cybersecurity
Marshal says six botnets are responsible for 85 per cent of spam
Paki takes down youtube
DARPA Drops $38M on Virtual Satellite Network
AT&T says cyber pearl harobr possible.
My Cyber attack on USA. Asterisk.Gerald
. .
or
"Connection timed out"
For Weeks:

Map By major ISP's.
no bombs, rootkits, explosions, hacking or announcement of war.
The Internet is designed to survive a nuclear attack to a few countries.
If a Continent or two are taken out by nuclear attacks the Internet will automatically rout around the missing pieces.
A DOS attack , as we know it now, targets a single URL, floods it with traffic
so visitors cannot get in.
A bot attack form a botnet, thousands of zombie computers attacking the one URL.
But suppose a Government with millions of zombie computers flooded a high volume Internet hub, and the hub above it and below it.
Ok now pick out a thousand of the key hubs to flood, with millions of botnets.
Now the traffic will try and work its way around the blockage and over welm some of the Internet shortcuts.
The effect would be some of the hubs would go down, and some would turn high speed T1 lines into dialup speeds.
The cascading effects could take out land line phones, cable TV, automated radio stations, back up banking transactions, close down shopping carts...
The traffic on the outer rings, and short cuts between hubs would also be flooded by the traffic routing around the blockages.
Are there a Million botnets out there?
WE DON'T KNOW, WE ONLY COUNT THE ACTIVE BOTNETS.
As a nation state someone could create 100,000 bots a day test 1,000 of them and let the rest sleep. No one would ever know about the sleeping botnets till they came on line.
Wait for the traffic to route around the blockages then take out another 1000 hubs, based on traffic patterns, for maximum effect.
The Internet could not be shut down, but the traffic making its way through the internet could be cut down this way by many many factors.
 Black nodes are "MIL" 1998
Black nodes are "MIL" 1998
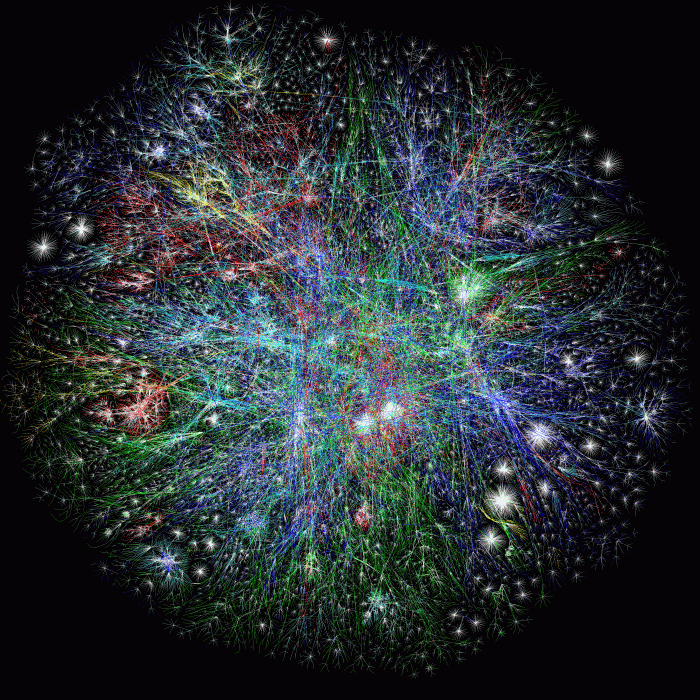 Global Nodes:
Global Nodes:
Our current measurement system does not account for "sleeper bots", only active bots.

Think your PC is slow now??
USA is not ready for this, nor does USA have this offensive capability.
Lots of work to do.
Gerald
UPDATE:
DDOS on DNS: Stopping Internet blackouts
| Writing in National Journal’s Technology Daily, Andrew Noyes discusses the possibility of a massive Internet blackout caused by a distributed denial of service (DDOS) attack on the backbone infrastructure of the ‘Net. |
| This type of high-tech ambush, which occurs when multiple compromised systems flood the bandwidth or resources of a targeted server to make Web pages unavailable, could be devastating for global online communication, said Susan Crawford of the Internet Corporation for Names and Numbers. |
October 22 2002 Nine of the internet's 13 "root DNS" servers are disabled in a massive attack by a bot herder advertising his services.
2006 Peer-to-peer communication protocols pass command of the botnet between compromised PCs to evade bot hunters. Automated retaliatory attacks start on anything trying to find or interfere with a botnet.
SOURCE:
xxxxxxxxxxxxxxxxxxxxx
China ‘has .75M zombie computers’ in US19 Sep 2007 by google soft
China ‘has .75M zombie computers’ in US. A former senior US information security official says there are nearly three-quarter million personal computers in the United States taken over by Chinese hackers. ...
xxxxxxxxxxxxxxxxxxxxxx
CHINESE HACKER:
Tan Dailin lets out an audible gasp when he is told that he was identified in the U.S. as someone who may have been responsible for recent security breaches at the Pentagon. "Will the FBI send special agents out to arrest me?" he asks. Much as they might want to talk with him, though, FBI agents don't have jurisdiction in Chengdu, the capital of China's Sichuan province, where Tan lives.
SOURCE: time inc
Gerald
Anthropologist
Hackers we have taken out: Here
The useful future of Cyber warfare.
WWW Terrain Map
Worst CASE:
Internet status check
RED ALERT new WWW attack paradigm
Internet Anthropologist available for Blog interview, Phone consult: or lecture.
UPDATE: 12.17.07
The suspicion remains that botnet time was rented to attack Estonia from Russian trans-national criminal syndicates and when this time ran-out the attacks fell-off. Since January 2007 numerous computers have been infected by a virus known as, Storm Worm, giving the criminal syndicates controlling the virus and hence the computers, processing power estimated beyond the power of the worlds top ten supercomputers. There is clearly an argument for using these botnet systems for more than just spam. It is not yet true to say that the next conflict will be fought virtually on computers alone but it may be rehearsed there.
SOURCE:
xxxxxxxxxxxxxx
UPDATE: 12.18.07
A senior Estonian official recently said for the first time that the cyberattacks earlier this year against his country's government and commercial Internet infrastructure were carried out using a network of computers infected with special hacker software that had been rented from a criminal syndicate.
Jaak Aaviksoo, the Estonian minister of defense, told a Washington audience last month that the botnet that attacked Estonia was "rented for that purpose and rented (from) clearly illegal groups that have hijacked a number of computers worldwide."
SOURCE:
UPDATE: 12.18.07
....
Ridentem dicere verum quid vetat....
FSB ( Russia ), HOW LONG BEFORE THE TALKING BOTS MIGRATE TO THE CELL PHONES? Phone service DDOS?
g
New threat matrix.
Update:01.08.07
The Strategy Page describes how China assembled a force few have heard about. In idyllic 1990s, the Chinese Defense Ministry established a research organization called the "NET Force" geared towards conducting information warfare. NET Force was soon joined by an irregular civilian militia; the "Red Hackers Union" (RHU). "Starting in the late 1990s, China assembled what has now become 30,000 Ministry of Public Security employees manning the Golden Shield Project (also known as The Great Firewall of China), and monitor Internet use throughout the country."
Future:
Infection and Survival
The initial infection of botnet client machines was done via worms, but soon the botnets began replicating themselves. Most botnets have the ability to self-update. The bot herder will issue an update command, and all his little troops will download and run new versions of themselves. This update mechanism is even more efficient than Windows update, and it's certainly frightening. Some viruses have also been known to disable antivirus software, and most users would never even notice. If a virus can successfully disable all defense mechanisms and then install undetectable bot client software, it's sure to survive.
The botnet itself is also a worm, because many bots have the ability to spread. They will try a fairly large arsenal of exploits against computers on the same network, or possibly even across the Internet. Bot clients updating themselves were primarily used as a mechanism to distribute new exploit code at first, but then something marvelous happened, and the first self-preservation behavior documented occurred recently: bot clients began DDoS'ing any computer that attempted to detect them by scanning. ( This cause the first massive attack against the NODES. It was an accident G)
Botnets have been dubbed "IRC Botnets" in the past, but this isn't completely accurate any longer. Some newfangled botnets still use IRC to communicate, but they do it over SSL. This essentially means that you cannot detect their presence. Furthermore, the old IRC model of "connect to a server" just isn't feasible. A distributed system that's dependent on a single server is useless, especially when that single server is a huge takedown target. Many a botnets were abandoned in the infancy stage of botnet evolution. We could see this with network anomaly detection tools quite easily: clients would appear as a TCP scanner when they unsuccessfully tried connecting to home-base over and over again.
At this point only one thing comes to mind: peer-to-peer applications. P2P networks have successfully thwarted the MPAA/RIAA, so it should work for botnets as well. Especially with their ability to replicate and attack back, they should be unstoppable. Indeed, there have been many reports of p2p botnet activity. Throw SSL in the mix, and they certainly are undetectable and unstoppable.
Let's think about this for a moment. If bots have the ability to self-update, self-preserve, and massively execute large parallel jobs at the command of a single person, what do we really have here? This is not just a tool for spamming and other ills; this is a living, breathing ecosystem.
SOURCE:
xxxxxxxxxxxxxxxxxxxxx
The result is that millions of business and home computers – some estimates put the figure as high as 300 million – have been taken over by global gangs of cyber criminals. They're being used every moment of the day for extortion, to spread child pornography and, most commonly, to spew out billions of unsolicited e-mails. It can – and has – brought down the internet for an entire country.
The problem is getting so bad, and accelerating so rapidly, some experts believe 2008 could even be the year the internet meets its Armageddon. On Christmas Eve and Hogmanay, unusually heavy botnet activity was reported, leading to speculation that a major attack was brewing.
SOURCE:
XXXXXXXXXXXXXXXX
Updated: 01.25.08
Malware Increased by 6 Orders of Magnitude from 2006 to 2007
xxxxxxxxxxxxxxxYOU CAN SAVE THE INTERNET !
Another free security utility: Trend Micro’s RUBotted
ZDNet Blogs -
RUBotted monitors for remote command and control (C&C) commands sent from a bot-herder to control your computer.
xxxxxxxxxxxxxxxx
PandaLabs: Half a Million Computers Infected with Bots Everyday
IT News Online Staff
2008-01-19
According to data compiled by PandaLabs in its annual report on malware activity in 2007, around half a million computers are infected by bots everyday.
Bots are programs that go resident on a computer awaiting commands from their creators, who can take complete control of the infected system. Once they have control over several hundred computers, cyber-crooks can hook them all up to create botnets.
The report said that approximately 11% of computers around the world are part of these botnets, and they are responsible for 85% of all spam sent.
SOURCE:
xxxxxxxxxxxxxxxxx
Couple a huge bot net attack with a physical cable attack:
( Internet failure hits two continents: Story Highlights: Extensive Internet failure has affected much of Asia, the Middle East, north Africa )
DUBAI, United Arab Emirates: 1.08 (CNN) -- Large swathes of Asia, the
>> Middle East and north Africa had their high-technology services
>> crippled Thursday following a widespread Internet failure which
>> brought many businesses to a standstill and left others struggling to cope.
Update: 3 cables cut in two days.
xxxxxxxxxxxxxxxxxx
DHS cyber storm test misses key TESTS. instant issues not pertinent.??
xxxxxxxxxxxxxxxxxxxxx
Is the Russian Business Network protected by the Federal'naya Sluzhba Bezopasnosti (FSB)? ( Internet Anthropologist hypothesised about this months ago.)
xxxxxxxxxxxxxxxxAmerican Teen with 400,000 bots.
xxxxxxxxxxxxxxxxxx
New class of WMD bots
xxxxxxxxxxxxxxxxxxx
There are defensive options, and offensive options, we have NOT discussed here.
Out of the Box solutions. Email me for details.
barb.andrews at gmail.com
UPDATE:12.28.2015
ISIS tried this through a Islamic News APP
NODES READY:NO PROBLEM
Gerald
Anthropologist
Tactical Internet Sys analyst.
AD MAGNUM
.
Botmaster owns up to 250,000 zombie PCs (9 November 2007)
Alleged CastleCops DDoS botmaster busted (3 October 2007)
FBI logs its millionth zombie address (13 June 2007)
Florida 'botmaster' charged with Akamai DDOS attack (24 October 2006)
Botnet master jailed for five years (9 May 2006)
Bot herder pleads guilty to 'zombie' sales (24 January 2006)
Suspected bot master busted (4 November 2005)
35 million bots and counting, 03,07.09
.
18-year-old alleged botnet king appears in New Zealand court
DHS gives itself a 'C' for cybersecurity
Marshal says six botnets are responsible for 85 per cent of spam
Paki takes down youtube
DARPA Drops $38M on Virtual Satellite Network
AT&T says cyber pearl harobr possible.
My Cyber attack on USA. Asterisk.Gerald
. .
Labels: attack, CYBERhttp://www.blogger.com/img/gl.link.gif, dos, HARBOR, PEARL, war




1 Comments:
It already exists and there is a good probability this is it:
The misnamed Storm Worm isn't actually a worm; it's a bot, used to corral infected computers together into a network called a botnet, which can then be issued commands by a central criminal controller. One common command is to send vast amounts of spam.
Also
The Storm Worm is capable of launching DoS attacks, and has already been used for them.
Post a Comment
Subscribe to Post Comments [Atom]
<< Home