WarIntel Bot probe
Our COWs have been busy.
And turned it over to Counter Surveillance.
They identified it as a small probing bot attack.
Fewer than 100. This is at least their second
probe.
Under our self defense paradigm,
this is an attack, computers controlled
by a third party, and our "rules of Engagement"
apply.
Barb looked at some of the Bots and they
have been infected Via Binary Planting.
by others. This was discovered in the wild again
a month ago.
Many Windows applications don't call DLLs using a full path name, but instead use only the filename, giving hackers wiggle room that they can then exploit by tricking an application into loading a malicious file with the same title as a required DLL. If attackers can dupe users into visiting malicious Web sites or remote shared folders, or get them to plug in a USB drive -- and in some cases con them into opening a file -- they can hijack a PC and plant malware on it.
Binary planting or DLL hijacking attacks have been known about for at least 10 years, and Microsoft was again informed of the problem in August 2009 by researchers at the University of California Davis.
This looks like a probing DOS attack, but as our
Binary planting or DLL hijacking attacks have been known about for at least 10 years, and Microsoft was again informed of the problem in August 2009 by researchers at the University of California Davis.
This looks like a probing DOS attack, but as our
blog is on Google servers they will be handling it.
We have deployed BSUs and remain vigilant
and are back tracking.
Cyber Weapons have been issued.
Barb is in a very good mood.
If you have trouble getting to our Blog,
you will know whats going on.
Gerald
Internet Anthropologist
Tactical Internet Systems analyst
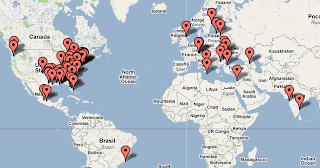
Locations of Bots:
One page.
IPs have been sanitized for privacy reasons.
IPs have been sanitized for privacy reasons.
We have 4 pages of these .
.



0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home